
How Product Security Helps To Protect Your Data at Egnyte
One of the critical challenges for organizations today is securing their data. Organizations must incur the cost associated with proper design, development, and maintenance of systems and their appropriate safeguarding and monitoring.
One way to reduce and optimize these costs is to choose tools that operate in a Software-as-a-Service model. Choosing tools in such a model helps shift some of the responsibilities and costs to the vendor. This model is called the Shared Responsibility Model, in which one of the critical assumptions is that the responsibility for development, maintenance, and product security rests with the service provider.
Egnyte puts great emphasis on data security and, therefore, on the security of its products. This article will discuss the basics of Product Security at Egnyte.
Product Security
Product Security is a set of practices, processes, or strategies to secure software products. It consists of various elements designed to address risk at multiple levels of the product, from the development process and system architecture to data security and end-user privacy.
These practices can be divided into many levels, areas, or processes. Below is a description of several key elements of Product Security at Egnyte.
Secure SDLC
The Software Development Life Cycle (SDLC) is a term that describes the software development process. This process is divided into several phases in which products, features, or services are developed. To ensure the most effective implementation of security, it must be an integral part of each stage.
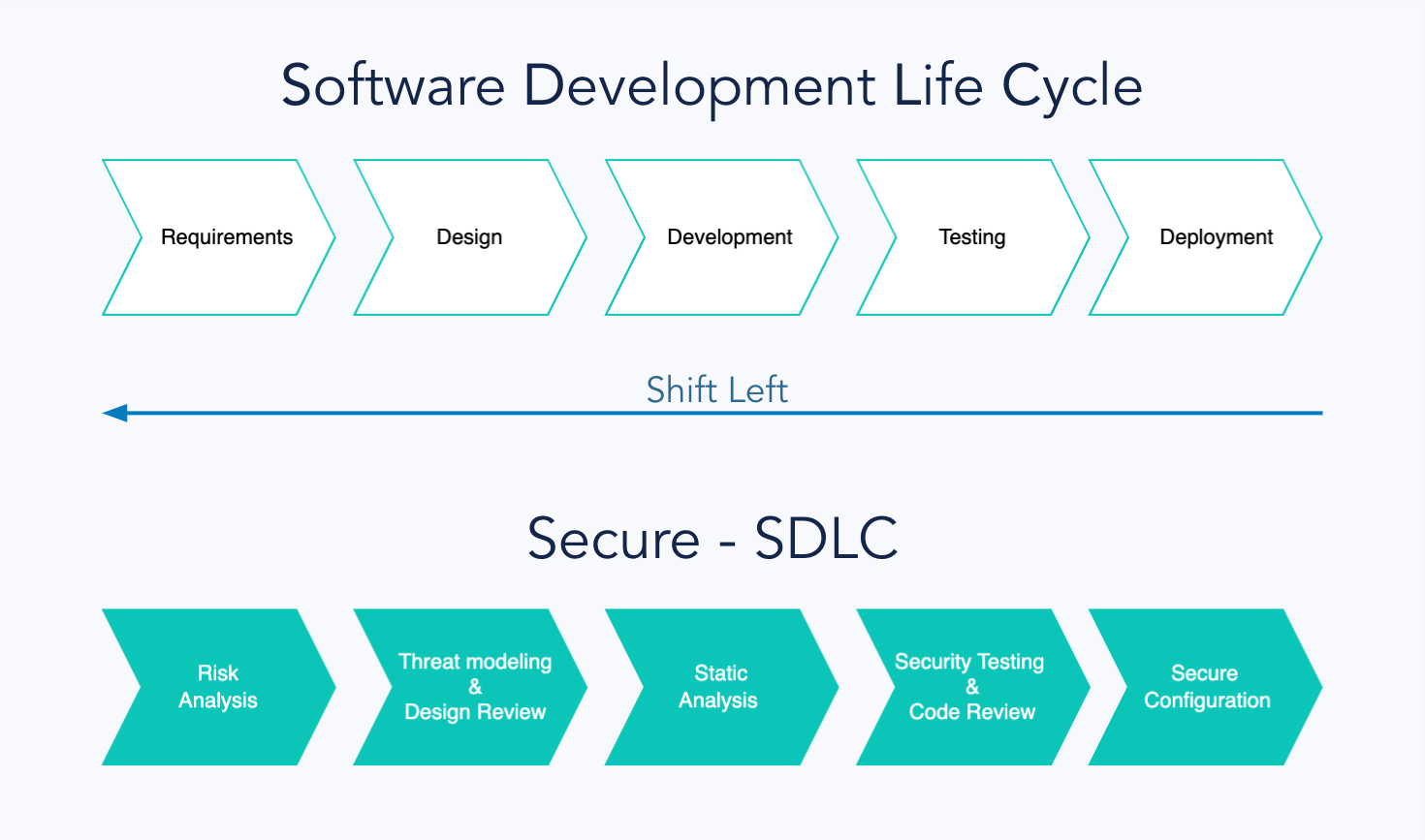
As the chart above demonstrates, security adds elements that support product development at various stages. These practices are adapted to each phase to become an integral part. In this way, security does not hinder or slow down the production process but supports it!
Shift-left
One of the critical assumptions of Secure SDLC is the optimal detection of security issues both in terms of cost and speed.
Detecting vulnerabilities and security issues when a product or feature is already operational is very important but not optimal. Removing such vulnerabilities can be very expensive due to their high complexity.
To be as efficient as possible in detecting and removing threats and problems, we adopt the shift-left approach at Egnyte. Product security engineers collaborate with development and product teams from the moment of defining assumptions and designing architecture to detect potential problems as early as possible and then remove or mitigate them. In this way, the solutions being built can be secure by design.
Vulnerability Management
No system is 100% free of vulnerabilities or bugs. Nonetheless, it's essential to strive toward that holy grail relentlessly. A crucial tool in this journey is the vulnerability management process.
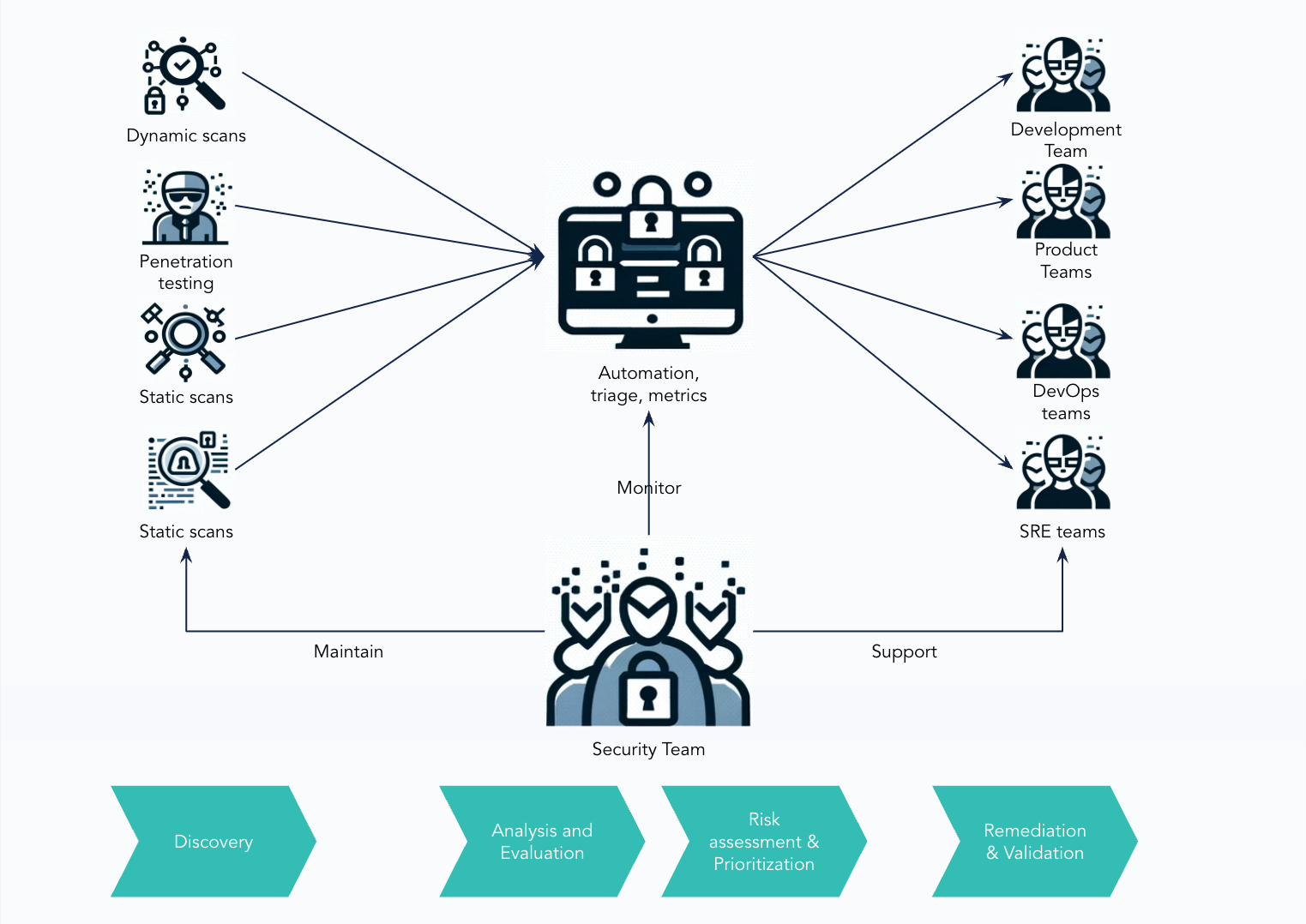
Vulnerability Management is a process aimed at quickly and effectively detecting vulnerabilities to enable a fast method of removing them from the product. So, effectiveness is crucial here. To make it possible at Egnyte, vulnerability detection in the development process takes place in several ways:
- Static Application Security Testing (SAST)
- Software Composition Analysis (automated dependency analysis)
- Dynamic System scanning while it is in operation
- Internal manual security analyses such as Secure Code Review, Pentests, and Architecture Reviews
- Sign-offs review for individual features
- External Pentests conducted by third parties.
All of the mentioned elements are a source of information about vulnerabilities. The product security team then reassesses detected vulnerabilities. Afterward, they are directed to the project teams, where they are eliminated.
Automating Security
The number of elements in the SDLC process is vast. This means a lot of work for the security team. The team must have the ability to respond quickly and dynamically prioritize work. To make this possible, security automation and related business processes are necessary.
To accomplish this, the security team should utilize every opportunity to implement automation. From automatic static and dynamic code, and configuration analyzers through infrastructure scanners, to automated risk monitoring or software releases.
Automation facilitates security management, accelerates response time, increases team capacity, and, most importantly, does not impede the development of our products!
Partnership with Engineering
Security is everyone's responsibility, not just that of the security team. This rule applies to every area and every organization. The same applies to the building of digital products and software.
In this case, development teams play a crucial role in implementing security. Continuous cooperation between the development and security teams is necessary to do this effectively. The basis of the product security team's operation is collaboration and partnership with development and engineering teams.
We, therefore, work based on a consulting approach, wherein, we advise engineering teams on the most optimal solutions. These are optimal not only in terms of security but also from a business point of view.
Such an approach requires a mutual understanding of the scope of work, business context, and priorities. It allows for finding the fastest possible solutions to detect challenges in existing code and identifying potential threats even before any code is created.
Examples of such practices include product requirement analysis and threat modeling, which the security team carries out with developers. Thanks to this element, emerging functionalities or services can be created based on the concept of ‘Secure By Design’. This concept implies that security is an integral part of the production cycle from the earliest conceptual stage.
Furthermore, the cooperative approach forms the foundation for building a DevSecOps culture, which aims to strengthen the awareness of all roles and functions involved in the software development process and enhance its flexibility, knowledge flow, and, of course, the quickest possible release cycle.
The Team
A crucial element necessary to achieve all of the above areas is the right team. Therefore, the team and engineers working in the product security team must have excellent expertise and experience in many areas. Starting with matters related to offensive security such as:
- Penetration testing in areas such as Web, Cloud, Mobile, or Desktop
- Secure Code Review
- Architecture and configuration review.
They also need knowledge of defensive security or security engineering such as:
- Security automation in CI/CD pipelines
- Threat modeling and risk assessment
- Designing security architecture.
To this, one must add expert knowledge spanning areas like Compliance, Software Engineering, IT System Architecture, and Fraud Prevention.
At Egnyte, we also place great importance on ensuring that the security team and its competencies reflect the needs and dynamics of product and engineering teams. Therefore, not only hard skills are essential to us, but soft skills as well. Our team's key competencies are communication and ownership over various cross-team initiatives.
Competencies in these areas are necessary to effectively cooperate with other teams and reduce friction in communication, and competency silos. This way, a partnership model in building secure software delivers the best results.






